Last weekend I wrote a post about the Reject Shop IP camera that was being sold for $39. I decided to have a deeper look at it to see if I could use it without relying on the app.
Portscanning
The first thing I did was do a portscan on it to see if I could get access to the underlying OS on the camera at all.
Unfortunately the only port that was open was TCP port 54321. Telnetting to this port revealed that it’s a debug console of some sort.
It would output regular updates about the camera, but didn’t give me much info about the underlying OS.
�do_log_ack�jfg_debug: connected.
��do_log_ack�cjfg_rtpserver_update_perf(delta=5006000, s=185, l=0, rate=0.0 OldBps=256Kbps NewBps=264Kbps wfi=0)
��do_log_ack�n01-01 00:02:13 CID=200000111111 UP=2:13 S#=1948 F#=1934 V=39913 AO=8606 AI=7 RA=0 RV=0 R=0 FPS=15 MD=0 CPU=0%
��do_log_ack�I[ntp.c : 222] ntp resolve server address [ntp.jfgou.com] failed: 11
��do_log_ack�cjfg_rtpserver_update_perf(delta=5073967, s=192, l=0, rate=0.0 OldBps=264Kbps NewBps=272Kbps wfi=0)
��do_log_ack�I[ntp.c : 222] ntp resolve server address [ntp.jfgou.com] failed: 11
��do_log_ack�cjfg_rtpserver_update_perf(delta=5005533, s=194, l=0, rate=0.0 OldBps=272Kbps NewBps=280Kbps wfi=0)
��do_log_ack�o01-01 00:02:23 CID=200000111111 UP=2:23 S#=2101 F#=2084 V=41658 AO=8588 AI=10 RA=0 RV=0 R=0 FPS=15 MD=0 CPU=0%
��do_log_ack�I[ntp.c : 222] ntp resolve server address [ntp.jfgou.com] failed: 11
��do_log_ack�cjfg_rtpserver_update_perf(delta=5076944, s=197, l=0, rate=0.0 OldBps=280Kbps NewBps=288Kbps wfi=0)
��do_log_ack�I[ntp.c : 222] ntp resolve server address [yun.jfgou.com] failed: 11
��do_log_ack�cjfg_rtpserver_update_perf(delta=5005378, s=195, l=0, rate=0.0 OldBps=288Kbps NewBps=296Kbps wfi=0)
I was hoping it would at least tell me something about the camera, or some way of connecting to it without relying on the App, but no luck there.
However, it does show something interesting when tapping on the camera in the app.
�do_log_ack�,jfg_ctrl: recv message, magic=4D4A, id=1004
��do_log_ack�,jfg_ctrl: recv message, magic=4D4A, id=1004
I’m assuming must be a message to the camera. I’ve blocked the camera from the internet, so when I tap on the camera, I get a ‘Device is off-line’ screen…but when I tap that, it will still connect to the camera, and I get the below output from the debug console.
��do_log_ack�,jfg_ctrl: recv message, magic=4D4A, id=1004
��do_log_ack�,jfg_ctrl: recv message, magic=4D4A, id=1007
��do_log_ack�tjfg_ctrl: play request, call id=[0] url=[18950:8880], target=[192.168.x.x], parsed=[18950:8880] (fixed port=8888)
��do_log_ack��jfg_rtpserver: do_connect(call_id=0, channel_id=16384, local=[VideoPort=0, AudioPort=0], target=[IP=192.168.x.x, VideoPort=18950, AudioPort=18950])
��do_log_ack�jfg_rtpserver_play_live()
��do_log_ack�!jfg_rtpserver_update_perf(reset)
��do_log_ack�4jfg_rtpserver: request key frame, timediff=48489822
So it seems like the app must be sending requests to it and then the camera responds and allows the app to connect to it. If I find someway to duplicate this handshake, then I should theoretically be able to connect to the camera.
Taking it apart
Since I didn’t get very far with the console, I decided to take the camera apart.
Taking it apart was pretty easy, the rubber cover on the bottom half can be pulled off, and then there’s 4 screws on the back to undo.
Undoing the screws and prying the cover off reveals the PCB of the camera. There is also a cable from the speaker in the back of the camera to unplug. I noticed that there was a reset button on the camera, which isn’t actually accessible from the outside of the camera.
Next to the camera is a set of jumper-holes. I’m guessing this is a SPI interface as I couldn’t get anything out of this port via my USB to TTL adapter.
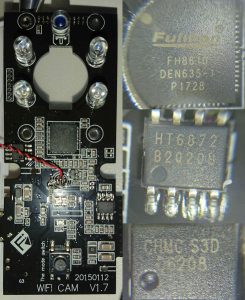
You can also see the WiFi module soldered onto the PCB. The camera uses a Marvell 88W8801-NMD2 chip, attached to a little tiny antenna. The camera is mounted on 4 posts, which are in turn mounted into the case of the camera. I took the camera off so I could have a look at the other side of the PCB.
On the otherside is where the main SoC for the camera is. At the top of the PCB is the 4 IR LEDs and the light sensor. The big chip right under where the camera would stick out is the SoC,
a Fullhan FH8610. It seems to be a 32bit CPU with a hardware H264 encoder, and I2C, SPI, GPIO, PWM, UART, and SDIO input/outputs. The HT6872 seems to be the audio chipset, and the CHMC S3D D6208 is a driver. You can see “the mode switch” down the bottom, which corresponds to the WiFi button on the outside. You can see the “WIFI CAM V1.7” and what I’m assuming is the date of manufacture at the bottom of the PCB too.
No interfacing 🙁
Apart from the pins labelled 3.3V, GND, RXD, TXD, CLK, CS, I couldn’t see any other way to interface with this camera. I was hoping that I could gain access to it when I opened it up so I could poke around and perhaps open ports or connect directly to the camera without going through the app. The SoC datasheet didn’t give me much help either. I guess I’ll have to try and mangle up a handshake to try and convince it to let me connect through RTP.



Have you gone any further with this? I have the same camera and have poking around. Someone had put a firmware.bin that I found in my travels, though I’m not sure if it is for the same camera, it’s has some ssid’s of DOG_??? like this camera. https://reverseengineering.stackexchange.com/questions/15088/lzma-file-format-not-recognized-details-enclosed. There was also a hard coded 192.168.101.6:8000 that I’m not sure how that plays into anything. Please ping me if you have any update.
I’ve bought a SPI logic analyzer so I can poke the TXD/RXD/CLK pins when I have some time. I’ll post an update if I get anywhere with it.
Also, I wouldn’t be surprised if that hardcoded IP address is something to do with the initial camera setup…I might reset mine back to defaults and try and connect a pc to the default wifi network to see if I can poke the camera some more that way too.
BTW. The original version (I think) is Clever Dog.
got it working over lan using blustacks to emulate the app
Hello! I was fiddling around with a cheap camera I recently bought. Checking it with nmap revealed the same 54321 debug port and output. After trawling the web some, I came across your article here, and as far as I know you’re the only one who has written about this camera.Just like you I can’t seem to get access to the OS of the camera, now I was wondering if you ever did get anywhere with the logic analyzer?
Cheers,
Tom
Hi Tom,
I haven’t had the time to even play with the logic analyzer unfortunately.
I had the idea of connecting to the camera with a laptop rather than a phone during initial setup, but haven’t had the time to try that yet either.
Let me know if you make any progress!